Introduction
In the fast-paced world of cloud computing, businesses are embracing the versatility and scalability that come with it. However, with great power comes great responsibility—especially when it comes to security. While many organizations focus on advanced threats and malicious attacks, a growing concern lurks in the shadows: misconfigurations. These seemingly innocuous mistakes are emerging as the new data breach, exposing sensitive data and leaving companies vulnerable to important repercussions. But don’t worry; there’s a silver lining! Enter Cloud Posture Management (CPM), a proactive approach that helps organizations identify and rectify these misconfigurations before they turn into costly disasters. In this article, we’ll explore why misconfigurations are a pressing issue and how adopting effective CPM practices can safeguard your cloud environment, ensuring that your business remains secure and compliant in an increasingly complex digital landscape. Let’s dive in!
Understanding the Rising Threat of Cloud Misconfigurations
As organizations increasingly migrate to the cloud, the complexities of managing cloud infrastructure grow considerably. Cloud misconfigurations have emerged as a leading cause of data breaches, surpassing traditional vulnerabilities. With the rapid adoption of cloud services, the attack surface has expanded, and the potential for human error has never been higher. This shift makes understanding and mitigating misconfigurations crucial for any association relying on cloud technology.
One of the primary challenges with cloud misconfigurations is the sheer variety of services and settings available. Each cloud provider offers a multitude of options, each with its own unique configurations. Here are some common misconfigurations that can lead to severe security risks:
- Exposed storage Buckets: Publicly accessible storage can lead to unauthorized data access.
- Improper IAM Roles: Over-permissioned roles can give users access to sensitive data they shouldn’t have.
- Unrestricted Security Groups: Firewalls that allow traffic from any source can leave networks vulnerable to attacks.
To combat these risks, organizations are turning to Cloud Posture Management (CPM) solutions. These tools help identify misconfigurations across various cloud environments, providing actionable insights that can significantly reduce risk. Here’s how CPM can definitely help:
- Continuous Monitoring: CPM solutions offer real-time monitoring of cloud configurations, ensuring immediate detection of any abnormal changes.
- Automated Compliance Checks: They assist in maintaining compliance with industry standards by regularly auditing configurations.
- Risk Prioritization: CPM tools can rank misconfigurations based on the level of risk, helping teams focus on the most critical issues first.
Integrating a CPM solution into your cloud strategy is not just about preventing misconfigurations; it’s about fostering a culture of security awareness across your organization. Regular training and updates on best practices for cloud usage can empower your teams to make informed decisions and reduce the likelihood of errors that lead to breaches.
as the threat landscape evolves, the need for effective cloud security measures is more critical than ever. Understanding the nuances of cloud configurations and investing in robust management solutions can definitely help organizations safeguard their data against the rising tide of misconfiguration threats.

Why Misconfigurations Are Often Overlooked in Security Strategies
In today’s fast-paced digital landscape, organizations often prioritize flashy security measures over the underlying configurations that can lead to vulnerabilities. Misconfigurations, however, are a silent yet formidable threat that frequently evade attention in thorough security strategies. Here’s why these oversights happen and how they can undermine even the most refined defenses.
Complexity and Overload
As systems become increasingly complex, the likelihood of misconfigurations rises. IT teams are often inundated with a myriad of platforms, tools, and settings to manage. This overload can lead to:
- Human Error: Mistakes during configuration processes, often due to fatigue or lack of training.
- Assumptions: Relying on defaults without realizing they may not be secure.
- Neglect: Overlooking less popular or legacy systems that still hold sensitive data.
Lack of Awareness
Many organizations focus their training and awareness programs on high-profile threats like phishing or ransomware, leaving a blind spot for misconfigurations. Without specific training on the importance of correct configurations, employees may be unaware of how easily these errors can lead to data breaches. This lack of awareness can result in:
- Inconsistent Practices: Variability in how configurations are managed across teams, leading to gaps in security.
- False Sense of Security: Believing that other security measures are sufficient when, in reality, misconfigurations can easily bypass them.
Rapid Deployment and Iteration
The modern approach to technology encourages rapid deployment and constant iteration, which can inadvertently introduce configuration errors. As organizations race to innovate, they may prioritize speed over security, leading to:
- Temporary Solutions: Quick fixes that are never properly secured or documented.
- Legacy Systems: Old configurations that remain in place and become increasingly insecure over time.
- Inadequate Testing: Insufficient testing of new systems or updates that fail to identify configuration issues.
Table: Common Misconfigurations and Their Impact
| Misconfiguration | Potential Impact |
|---|---|
| Open Storage Buckets | Data exposure to unauthorized users |
| Default Credentials | Easy access for attackers |
| Misconfigured Firewalls | Unauthorized network traffic |
| Improper IAM Policies | Excessive permissions for users |
As organizations shift to the cloud, they frequently enough overlook the importance of a robust configuration management strategy. Cloud environments can be particularly susceptible to misconfigurations due to shared responsibility models, which can create confusion about who is responsible for security. This underscores the need for organizations to adopt proactive measures that prioritize configuration management as part of their core security strategy.
Ultimately, by acknowledging and addressing the root causes of misconfigurations, organizations can significantly enhance their security posture. Implementing tools like cloud posture management can help automate and streamline the monitoring of configurations, ensuring that security is not just an afterthought but an integral part of the deployment process.
The Costly Consequences of Cloud Misconfigurations
In the ever-evolving landscape of cloud computing, misconfigurations are emerging as a silent yet formidable threat.The shift from traditional data breaches to these overlooked configuration errors can have profound implications for organizations of all sizes. As businesses increasingly rely on cloud services, the complexity of these environments often leads to oversights that can expose sensitive data and systems.
Consider the following ramifications of cloud misconfigurations:
- Data Exposure: Misconfigured cloud storage can leave sensitive data accessible to unauthorized users, leading to potential data leaks.
- Financial Loss: Organizations can face hefty fines and legal fees due to breaches resulting from misconfigurations, especially under regulations like GDPR.
- Reputation Damage: A single misconfiguration can tarnish a company’s reputation,eroding customer trust and impacting future business opportunities.
- Operational Downtime: Misconfigurations may result in outages or degraded performance, affecting business continuity and productivity.
Moreover, the cost of these errors goes beyond immediate financial impacts. Companies can spend extensive resources on post-incident recovery efforts, diverting attention from innovation and growth.The ongoing need for vigilance can strain IT teams that are already stretched thin, leading to burnout and inefficiencies.
To illustrate the frequency and severity of these incidents, consider the data from a recent study:
| Year | Reported Misconfigurations | Average Cost of Breach |
|---|---|---|
| 2021 | 1,500+ | $4.24 million |
| 2022 | 2,000+ | $4.35 million |
| 2023 | 2,500+ | $4.45 million |
These figures highlight a growing trend that organizations cannot afford to ignore. As the number of reported misconfigurations rises, so does the accompanying financial burden. This begs the question: how can organizations safeguard themselves against these costly oversights?
Implementing effective cloud posture management is a proactive step in mitigating misconfiguration risks. By continuously monitoring cloud environments and enforcing best practices, organizations can:
- Identify vulnerabilities before they can be exploited.
- automate compliance checks to ensure configurations meet industry standards.
- Enhance overall visibility into cloud resources, enabling quicker responses to potential threats.
- Empower teams with tools and insights to maintain optimal security postures.
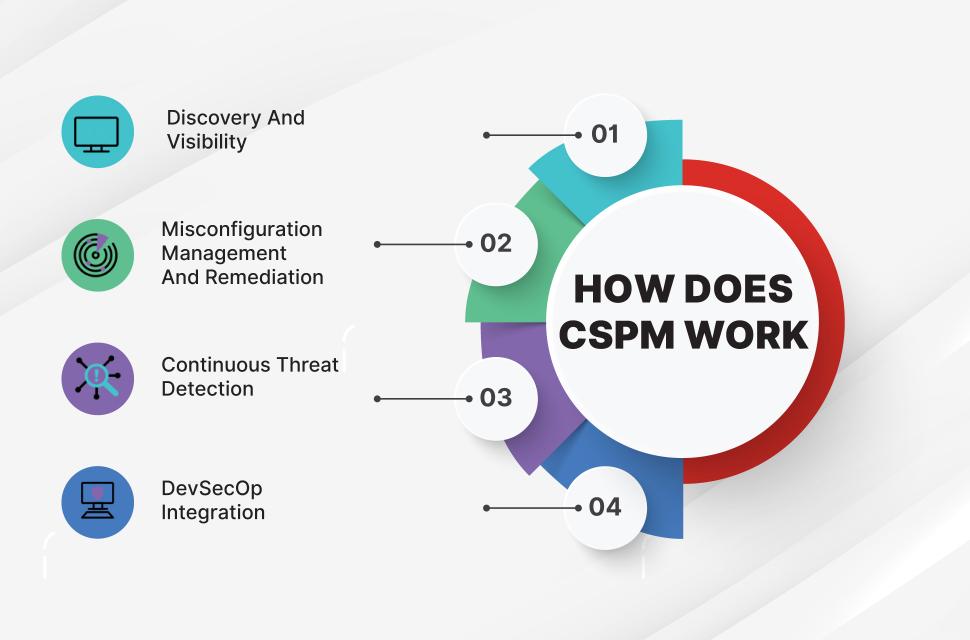
How Cloud Posture management Can Transform Your Security Approach
In today’s fast-paced digital landscape, cloud security is no longer a luxury; it’s a necessity. With an increasing number of organizations migrating to the cloud, the risk of misconfigurations has never been higher. These missteps can lead to vulnerabilities that cybercriminals eagerly exploit, often resulting in devastating data breaches. This is where Cloud Posture Management (CPM) steps in, offering a comprehensive solution to safeguard cloud environments.
Cloud Posture Management allows organizations to continuously assess their cloud configurations across various services. By implementing CPM, businesses can:
- identify vulnerabilities: CPM tools can automatically scan for misconfigurations and provide actionable insights, allowing companies to remediate issues before they become liabilities.
- Enforce compliance: Compliance with industry standards and regulations can be complex. CPM solutions simplify this by ensuring that cloud resources adhere to compliance requirements, reducing the risk of penalties.
- Enhance visibility: With a centralized dashboard, organizations can gain real-time visibility into their cloud posture, making it easier to monitor changes and respond swiftly.
moreover, CPM empowers organizations to adopt a proactive security stance. Instead of merely reacting to incidents, businesses can anticipate potential threats and adapt their security posture accordingly.This transition from a reactive to a proactive approach can significantly reduce the likelihood of security breaches.
Consider the following table that illustrates the benefits of integrating Cloud Posture Management into your security strategy:
| benefit | Description |
|---|---|
| Real-time Monitoring | Continuous oversight of cloud configurations and activities. |
| Automated Alerts | Instant notifications when potential misconfigurations are detected. |
| Comprehensive Reporting | Detailed reports for audits,compliance checks,and security reviews. |
| Risk Assessment | In-depth analysis of risk exposure based on current configurations. |
leveraging Cloud posture Management not only mitigates the risk associated with misconfigurations but also fosters a culture of security awareness within an organization. By prioritizing cloud posture, businesses can significantly enhance their overall security strategy, ensuring that they are not just defending against the latest threats, but are also fortifying their defenses for the future.
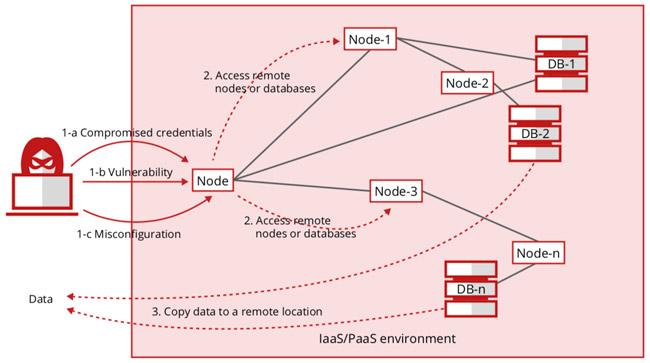
Identifying common Misconfigurations in Cloud Environments
In today’s cloud-centric world, identifying misconfigurations is crucial for safeguarding sensitive data and maintaining compliance. Many organizations overlook the importance of proper configuration,often leading to ample vulnerabilities. here are some of the most common areas where misconfigurations tend to occur:
- Inadequate Access Controls: Failing to implement the principle of least privilege can expose resources to unauthorized users. Ensure that only essential personnel have access to critical systems.
- Exposed Storage Buckets: Publicly accessible cloud storage can lead to data leaks. Regularly audit your storage configurations to ensure that sensitive information is adequately protected.
- Weak Security Group settings: Misconfigured security groups can allow unwanted traffic to flow in and out of your cloud environment. Tighten your security group rules to minimize exposure.
- unpatched Software: Running outdated applications can leave your environment vulnerable to exploits. Regularly update your software to stay ahead of potential threats.
- Overly permissive IAM Policies: Identity and Access Management (IAM) is essential for managing permissions across your cloud services. Avoid using wildcard permissions which can unintentionally grant excessive access.
Understanding these common pitfalls is the first step towards enhancing your cloud security posture. However, identifying these misconfigurations manually can be a daunting task. This is where cloud posture management solutions come into play. They provide automated tools that continuously monitor your configurations, ensuring compliance with best practices and regulatory requirements.
Consider the impact of human error in managing cloud configurations. A recent report highlighted that 80% of data breaches are due to misconfigurations rather than malicious activities. This staggering statistic emphasizes the need for proactive measures. by leveraging cloud posture management, organizations can minimize risk and maintain a robust security posture without the constant worry of oversight.
| Misconfiguration Type | potential Risk | Cloud Posture Management Benefit |
|---|---|---|
| Inadequate Access Controls | Unauthorized access to sensitive data | Automated access audits |
| Exposed Storage Buckets | Data leaks and breaches | Real-time storage monitoring |
| Weak security Group settings | Unwanted traffic | Security group best practice recommendations |
| Unpatched Software | Vulnerability to exploits | Automated patch management alerts |
| Overly Permissive IAM Policies | Excessive access | Policy optimization suggestions |
Investing in a cloud posture management solution not only helps identify and rectify these misconfigurations but also fosters a culture of security awareness within your organization. By empowering teams with the right tools and knowledge, you can dramatically reduce the risk of a data breach, ensuring your cloud environment remains secure and compliant.
Best Practices for Implementing Effective Cloud Posture Management
In the whirlwind of cloud adoption, organizations frequently enough overlook the importance of a robust cloud posture management strategy. To fortify your defenses against misconfigurations, consider these essential practices:
- Regular Audits: Conduct routine audits of your cloud configurations.Regular checks can definitely help identify vulnerabilities before they become exploitable.
- Automated Compliance Monitoring: Leverage tools that provide real-time monitoring and alerting for compliance standards relevant to your industry.
- Role-Based Access Control: Implement strict access controls based on user roles to minimize the risk of unauthorized changes to configurations.
- Change Management Processes: Establish a formal change management process to track modifications in settings, which helps in accountability and rollback if needed.
Another vital aspect of a accomplished cloud posture management strategy is a strong focus on education and training. Ensuring that your team is well-versed in security best practices can significantly decrease the likelihood of human error:
- Regular Training Sessions: Host training sessions that educate your teams about cloud security risks and mitigation techniques.
- Simulated Phishing Attacks: Conduct simulations to prepare employees for potential phishing attacks that could lead to misconfigurations.
- Documentation: Create accessible documentation on cloud security policies and procedures for reference.
To provide clarity and streamline processes,consider implementing a centralized dashboard that aggregates all cloud resources and their configurations. This can definitely help visualize the overall posture and identify areas needing immediate attention. Below is a simple portrayal of the dashboard components:
| Component | Description |
|---|---|
| Resource Inventory | List of all cloud resources and their configurations. |
| Compliance Status | Real-time status of compliance with security standards. |
| Alerts & Notifications | Instant notifications for misconfigurations or security breaches. |
Lastly, don’t underestimate the power of collaboration. Engage with cloud service providers and security experts to stay informed about the latest threats and best practices. Building a strong relationship with your vendors can yield valuable insights and enhance your overall cloud security posture.

The Role of Automated tools in Mitigating Misconfigurations
In today’s complex cloud environments, the challenge of misconfigurations looms large, often leading to vulnerabilities that can be exploited by malicious actors. Automated tools have emerged as essential allies in this battle against misconfigurations, providing organizations with the ability to proactively identify and rectify security gaps before they can be exploited.
One of the most significant advantages of automated tools is their ability to perform continuous monitoring without the fatigue that human oversight can incur. These tools can:
- Quickly Identify Misconfigurations: Automated systems can scan cloud environments to detect deviations from best practices and security baselines.
- provide Real-Time Alerts: With real-time monitoring, organizations can receive immediate notifications about potential risks, enabling swift remediation.
- Enhance Compliance: Automated compliance checks ensure that configurations adhere to industry regulations,reducing the risk of penalties and reputational damage.
Moreover, these tools frequently enough come equipped with sophisticated analytics capabilities that help organizations understand the root causes of misconfigurations. By analyzing patterns and historical data, automated tools can help teams recognize frequent mistakes and implement training or process improvements to prevent future issues. This approach not only enhances security but also fosters a culture of continuous enhancement within the organization.
Consider the following table that illustrates the comparison between manual checks and automated tools:
| Aspect | Manual Checks | Automated Tools |
|---|---|---|
| Speed | Time-consuming | Instantaneous |
| Accuracy | prone to human error | High precision |
| Scalability | Difficult to scale | Effortlessly scalable |
| Cost | Higher long-term costs | Cost-effective in the long run |
Ultimately, integrating automated tools into a cloud posture management strategy empowers organizations to maintain a robust security posture. By automating the monitoring and management of configurations,businesses can minimize the risk of breaches caused by human error and focus their resources on strategic initiatives rather than routine checks. As the landscape of cyber threats continues to evolve, the importance of these automated solutions cannot be overstated—it’s not just about responding to breaches, but about proactively preventing them.
Building a Culture of Security Awareness in Cloud Management
In today’s rapidly evolving digital landscape, fostering a culture of security awareness is no longer optional; it is essential. As organizations increasingly rely on cloud services, the potential for misconfigurations to become a significant threat rises sharply. When employees understand the importance of security and their role within it, they can definitely help mitigate risks before they escalate into costly breaches.
To cultivate this culture, consider implementing the following strategies:
- Regular Training Sessions: Conduct ongoing training sessions to keep employees updated on the latest security practices and potential threats. Use real-world scenarios to illustrate the impact of misconfigurations.
- Simulated Attacks: Organise phishing simulations and other security drills that help employees recognize and respond to potential threats, reinforcing their learning in a practical environment.
- Encourage Open Dialogue: Create a space where employees feel comfortable reporting security concerns or asking questions without fear of reprimand.
- Recognize and Reward: Acknowledge employees who demonstrate proactive security behaviors. Incentives can motivate others to follow suit.
Another crucial aspect of building a security-aware culture is integrating security protocols into everyday operations. This means that security should not be viewed as an add-on but rather as an integral part of the cloud management process. Here’s how:
| Cloud Management Activity | Security Integration Practice |
|---|---|
| Deployment | Use automated tools to check for misconfigurations before rollout. |
| Monitoring | Implement continuous monitoring with automated alerts for suspicious activities. |
| Access Control | Enforce the principle of least privilege to minimize exposure to risks. |
Moreover, leveraging Cloud Posture Management (CPM) tools can significantly enhance your security posture. These tools provide visibility into your cloud environment, automatically identifying misconfigurations and suggesting remediation strategies. By utilizing CPM, organizations can:
- Proactively Manage Risks: Identify vulnerabilities before they can be exploited.
- Automate Compliance: ensure that your cloud infrastructure adheres to industry standards and regulations effortlessly.
- Streamline Incident Response: Quickly address security incidents with real-time insights and alerts.
Ultimately, a culture of security awareness requires commitment from every level of the organization. When security becomes a shared responsibility, employees are more likely to recognize the significance of their actions in protecting sensitive data. Emphasizing the role of cloud posture management not only helps in identifying misconfigurations but also fosters a proactive security mentality among team members,leading to a safer and more resilient cloud environment.

Real-World Examples of Misconfigurations Leading to Data Breaches
Misconfigurations in cloud environments have become a significant concern, often leading to devastating data breaches. One high-profile example is the Capital One breach, which exposed the personal data of over 100 million customers. This incident resulted from a misconfigured web request firewall (WAF) that allowed a malicious hacker to exploit a vulnerability in the cloud infrastructure. The breach highlighted the critical need for continuous monitoring and management of cloud configurations to safeguard sensitive information.
Another instance occurred with Uber, where improperly configured Amazon S3 storage lead to the exposure of personal data for 57 million users and drivers. The root cause was a simple oversight: developers failed to set the appropriate permissions on the storage bucket, allowing unauthorized access. This incident not only compromised personal data but also resulted in severe reputational damage and financial penalties for the company.
Expedia also fell victim to a misconfiguration, where an unprotected Elasticsearch database was left exposed, leading to the breach of records for millions of users. this was a classic case where a lack of adequate security controls on cloud databases allowed unauthorized access. Such breaches underscore the necessity for organizations to implement robust security measures at every level of their cloud environments.
These examples illustrate common misconfigurations that can easily slip through the cracks:
- Exposed storage buckets: Leaving cloud storage unprotected and publicly accessible.
- Weak IAM policies: Overly permissive identity and access management settings.
- Open ports: Unrestricted access to services that should be limited.
To further emphasize the impact of these breaches, consider the following table that summarizes the key details:
| Company | Incident | Data Exposed | Impact |
|---|---|---|---|
| Capital One | Misconfigured WAF | 100 million customer records | Severe reputational damage, $80 million fine |
| Uber | Unsecured S3 bucket | 57 million user and driver records | Major fines, loss of trust |
| Expedia | Exposed Elasticsearch database | Millions of user records | Data loss, legal ramifications |
Each of these breaches serves as a powerful reminder that even a small misconfiguration can lead to catastrophic consequences. Implementing a robust cloud posture management strategy can significantly mitigate these risks, ensuring that your cloud environment remains secure and compliant. By proactively managing configurations, organizations can not only protect sensitive data but also enhance their overall security posture against an ever-evolving threat landscape.

Developing a Proactive Strategy for Cloud Security
In today’s fast-paced digital landscape, the cloud has become the backbone of many organizations. However, with great power comes great responsibility, and maintaining security in the cloud is more critical than ever. A proactive strategy for cloud security involves anticipating potential threats and taking measures to mitigate risks before they escalate. Misconfigurations, frequently enough seen as a minor oversight, can lead to devastating data breaches. Thus, adopting a robust cloud posture management approach is essential.
To build an effective proactive strategy, organizations should consider the following key elements:
- Continuous Monitoring: Regularly track cloud configurations to identify vulnerabilities before they can be exploited.
- Automated Compliance Checks: Utilize tools that automatically validate cloud configurations against industry standards.
- Incident response Planning: Develop a clear plan for addressing security incidents swiftly and effectively, minimizing potential damage.
- Training and Awareness: Invest in ongoing training for IT staff and end-users on security best practices to reduce human error.
- Regular Audits: Conduct scheduled audits to ensure compliance with security policies and identify areas for improvement.
One of the most effective ways to prevent misconfigurations is through the implementation of automated tools designed for cloud posture management. These tools provide real-time insights into the security posture of cloud environments,helping teams identify and rectify misconfigurations as they occur. By leveraging automation, organizations can significantly reduce manual effort and human error, which are frequently enough the root causes of security breaches.
Consider the following table, which outlines the benefits of adopting a proactive strategy with cloud posture management:
| Benefit | Description |
|---|---|
| Enhanced Visibility | Gain clear insights into cloud configurations, making it easier to spot vulnerabilities. |
| Faster Response Time | Automated alerts and response protocols expedite the resolution of security issues. |
| Cost-Effective | Reduce the financial impact of breaches by preventing them before they occur. |
| Increased Compliance | Stay aligned with regulations and industry standards, minimizing risk of penalties. |
Ultimately, is not just about the technology you implement; it’s also about fostering a culture of security within your organization. Encourage your teams to embrace security as a shared responsibility. By integrating cloud security into every aspect of your operations, from advancement to deployment, you can create a resilient environment that not only protects sensitive data but also instills confidence in your stakeholders.

Future-Proofing Your Cloud Infrastructure Against Misconfigurations
As organizations increasingly adopt cloud services, the risk of misconfigurations has become a significant concern. These misconfigurations, often overlooked, can lead to severe vulnerabilities, making it essential to prioritize cloud posture management. By establishing a robust strategy, businesses can effectively minimize risks and enhance their cloud security posture.
To begin future-proofing your cloud infrastructure, consider implementing the following best practices:
- regular Audits: Conduct frequent audits of your cloud environment.This ensures compliance with established security policies and identifies any misconfigurations before they can be exploited.
- Automated Tools: Leverage automated tools for configuration management. These tools can quickly pinpoint misconfigurations and suggest corrections, allowing your team to focus on more strategic initiatives.
- Role-Based Access Control (RBAC): Limit access to sensitive resources by implementing RBAC. This minimizes the risk of accidental or intentional misconfigurations by restricting who can modify settings.
- Continuous Monitoring: Establish continuous monitoring processes. Real-time alerts can notify your team of any changes or anomalies, ensuring rapid response to potential threats.
A critical aspect of cloud posture management is maintaining visibility into your entire cloud environment. organizations frequently enough struggle with this due to the sheer complexity and scale of their infrastructure. By utilizing a comprehensive dashboard, you can gain insights into configuration settings, user access, and overall compliance status. This visibility is vital for informed decision-making and proactive risk management.
Furthermore, engaging in regular training and awareness programs for your team can significantly reduce the likelihood of misconfigurations. consider organizing workshops that focus on:
- Cloud Best Practices: Teach your team the essential principles of secure cloud configurations.
- Incident Response: Equip them with the knowledge to respond effectively to security incidents resulting from misconfigurations.
- Collaboration Tools: Foster a culture of collaboration where team members can share insights and best practices.
Lastly, don’t underestimate the importance of documenting your cloud configurations and changes meticulously. A well-maintained documentation process not only aids in compliance but also acts as a reference to quickly revert any misconfigurations if they occur. Consider using a simple table format for tracking changes:
| Change Date | Changed By | Description | Status |
|---|---|---|---|
| 2023-01-15 | John Doe | Updated IAM policies | Completed |
| 2023-02-20 | Jane Smith | Configured VPC settings | In Progress |
| 2023-03-05 | Emily Johnson | Enabled logging for S3 buckets | Completed |
By emphasizing a proactive approach to cloud posture management and prioritizing these strategies,organizations can significantly reduce the risk of misconfigurations,thereby protecting their valuable resources and customer data in the cloud. Adapting to this mindset is not just a precaution; it’s a necessity in today’s digital landscape.

Key Takeaways: Strengthening Your Cloud Security Posture Today
Key Takeaways
Cloud security has transformed from a niche concern to a critical aspect of business operations. As organizations rapidly adopt cloud services, the potential for misconfigurations has skyrocketed, leading to vulnerabilities that can expose sensitive data. Here’s how to enhance your cloud security posture and mitigate these risks:
- Prioritize Continuous Monitoring: Implementing a robust continuous monitoring strategy enables you to identify misconfigurations in real-time. Tools that provide visibility into cloud environments can alert you to potential threats before they escalate.
- Embrace Automation: Utilize automated compliance checks to ensure your configurations align with best practices. Automation not only reduces human error but also streamlines the process of maintaining security standards.
- Implement Role-Based Access Control: Tailor user permissions based on roles to limit exposure to sensitive areas of your cloud infrastructure. This minimizes the risk of accidental misconfigurations and enhances overall security.
Understanding the common pitfalls that lead to configuration errors is essential. some typical areas of concern include:
| Common Misconfigurations | Impact |
|---|---|
| Open S3 Buckets | Data exposure to the public |
| Weak IAM Policies | Unauthorized access to resources |
| unrestricted Security Groups | Vulnerable to DDoS attacks |
To truly strengthen your cloud security posture, consider adopting a cloud posture management solution. These platforms offer:
- Real-time Configuration Insights: They provide a comprehensive view of your cloud resources and highlight compliance with security standards.
- Automated Remediation: Address misconfigurations automatically, ensuring that security policies are enforced without manual intervention.
- Risk Assessment Tools: Identify, assess, and prioritize risks associated with your cloud configurations, enabling informed decisions for remediation efforts.
Incorporating these strategies will not only fortify your security posture but also cultivate a culture of security awareness within your organization. By prioritizing proactive measures and leveraging the right tools,you can protect your cloud assets against the emerging threats posed by misconfigurations.
Frequently Asked Questions (FAQ)
Q&A: Misconfigurations Are the New Data Breach: How cloud Posture Management Helps
Q: What do you mean by “misconfigurations” in the context of cloud services?
A: Great question! Misconfigurations refer to incorrect or suboptimal settings in cloud services that can leave your data and applications vulnerable. This could be anything from leaving storage buckets publicly accessible to not applying proper security groups. Unfortunately, these misconfigurations are one of the leading causes of data breaches today.
Q: Why are misconfigurations often overlooked by organizations?
A: Many organizations focus heavily on the features and functionalities of cloud services but often neglect security settings. With the rapid adoption of cloud technologies, teams might rush to deploy applications without ensuring that configurations are secure. It’s a classic case of “move fast and break things,” but in this case, it can lead to serious security risks!
Q: How common are these misconfigurations?
A: Alarmingly common! Studies have shown that a significant percentage of organizations experience at least one misconfiguration-related incident each year. It’s estimated that misconfigurations account for a large portion of data breaches, making them as critical as more commonly recognized security threats like phishing or malware.
Q: What is Cloud Posture Management (CPM), and how does it help?
A: Cloud Posture Management is all about continuously assessing and managing your cloud security configurations. CPM tools automatically evaluate your cloud environment, identify misconfigurations, and provide actionable recommendations to fix them.Think of it as your cloud security guardian,ensuring that everything is configured properly and securely.
Q: Can you give an example of how CPM can prevent a data breach?
A: Absolutely! Let’s say your organization has an Amazon S3 bucket storing sensitive customer data. If that bucket is accidentally set to public, anyone can access it. A CPM tool would flag this misconfiguration, alert your team, and guide them to lock down the bucket before any unauthorized access occurs. This proactive approach can save you from potential breaches and the hefty costs that follow.
Q: Are there any specific challenges organizations face when implementing CPM?
A: One of the biggest challenges can be the sheer complexity of cloud environments. As organizations adopt multi-cloud strategies, it becomes increasingly difficult to keep track of configurations across different platforms. Additionally, some teams may lack the expertise to interpret CPM findings or take corrective actions. But the benefits far outweigh the challenges, especially when it comes to protecting sensitive data!
Q: What should organizations prioritize when adopting Cloud Posture Management?
A: First and foremost, they should focus on visibility. Understanding your cloud environment is crucial. Next, invest in tools that integrate seamlessly with your existing workflows and provide clear, actionable insights. ensure that your team is trained not just to use CPM tools, but also to understand the security implications of misconfigurations.
Q: How can organizations make the business case for adopting CPM?
A: To make a strong business case, highlight the financial and reputational risks associated with data breaches stemming from misconfigurations. Emphasize that investing in CPM can save money in the long run by preventing breaches,reducing compliance fines,and protecting brand trust. It’s about demonstrating that proactive security measures are a savvy investment,not just an expense.
Q: Any final thoughts?
A: Absolutely! With misconfigurations being the new frontier for data breaches, turning a blind eye is not an option. Cloud Posture management is not just a luxury—it’s a necessity for any organization that wants to protect its data and maintain customer trust. By prioritizing cloud security and leveraging CPM, you can stay ahead of potential threats and ensure a secure cloud environment.Don’t wait for a breach to happen—take action today!
Closing Remarks
As we wrap up our discussion on the rising threat of misconfigurations in the cloud world, it’s clear that understanding and addressing these vulnerabilities is more crucial than ever. In an era where data breaches can occur in the blink of an eye, taking proactive steps toward cloud posture management is not just smart—it’s essential.
By implementing robust cloud posture management solutions, you’re not only protecting your data but also safeguarding your reputation and bottom line. Remember, the cost of a breach isn’t just financial; it can impact customer trust and loyalty, which are invaluable in today’s competitive landscape.
So, let’s not wait for a misconfiguration to become a headline. Start prioritizing your cloud security today. Embrace the tools and practices that can help you identify vulnerabilities before they turn into costly breaches. After all, in the digital age, prevention is the best form of protection.
Stay vigilant, stay informed, and empower your organization to thrive in a secure cloud environment. Because when it comes to your data, the only breach that should be on your radar is the one you’re actively preventing.


